42Crunch Platform release, April 2, 2025
|
Platform version: v1.44.x |
This 42Crunch API Security Platform release introduces new look for viewing and editing Scan v2 configurations on the platform UI, and brings support for the OpenAPI Specification (OAS) v3.1 in API Scan to IDEs.
New features
The following are the new features and improvements to the existing ones in this release.
New look and feel for Scan v2 configurations in API Scan
We have overhauled scan configurations for API Scan v2 on the platform UI,
- Get a more structured view of the scan configuration, with dedicated tabs for different things.
- Edit scan configuration details and add new requests, scenarios, and other elements through dialogs on the UI instead of editing the raw JSON.
- Include requests external to your API as part of the scan configuration.
- Add tests for BOLA (Broken Object Level Authorization) or BFLA (Broken Function Level Authorization) into your scan configuration directly from the platform UI.
- Quickly change scan settings, like when configuring Scan v1.
- The presentation of the configuration on the platform UI has been aligned with scan configurations in IDEs so that you can easily switch between them.
For more details, see Scan configuration details.
OWASP API Security Top 10 2023 in the scan report
API Scan now also shows OWASP API Security Top 10 2023 vulnerabilities in the scan report, both for Scan v1 and v2. To see the 2023 vulnerabilities, you need to rerun the scan to get a new report.
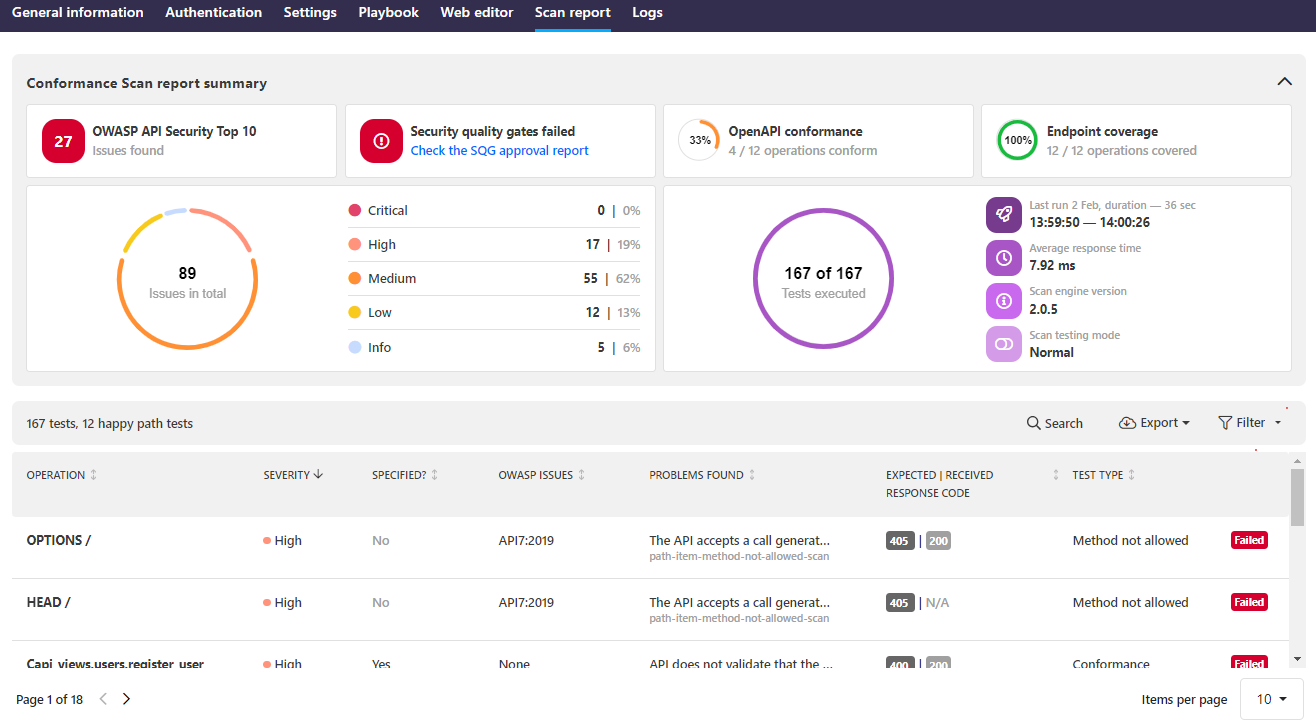
For continuity, we have also retained the existing vulnerabilities from the 2019 version. You can use the filters in the scan report to home in one the ones that you are interested in.
In addition, API Scan no longer runs tests on subschemas found in an anyOf construction, because the volatility of such constructs makes it too difficult to meaningfully test the API behavior. We have also improved how API Scan generates values for testing error handling on Boolean values.
Support for the OAS v3.1 in API Scan in IDEs
The IDE extensions for VS Code, JetBrains IDEs, and Eclipse now also let you scan OAS v3.1 APIs like OAS v3.0.x APIs. The Try It function now also works with OpenAPI 3.1.
In addition, you can now also export the latest audit and scan report from your IDE as JSON. For more details, see Integrate IDEs with 42Crunch Platform.
Improvements to the OAS v3.1 support in API Security Audit
We have improved Security Audit handles some issues in APIs following the OpenAPI Specification (OAS) v3.1:
- The properties
exclusiveMinimumandexclusiveMaximummust now be defined as numeric values, not Boolean like in OAS v3.0. If the properties have Boolean values defined in OAS v3.1, the issuev3_1-validation-property-value-typeis raised. - Defining the singular
exampleinstead of the pluralexamplesin schemas no longer raises a structural issue: even though the property has been deprecated, it is still present in the OAS v3.1.
We will continue to adapt Security Audit for the OAS v3.1 as well as implementing new checks for it in the coming releases.
Support for the OAS v3.1 in CI/CD plugins
We are releasing new major version for our REST API Static Security Testing CI/CD plugin to include support for the OAS v3.1 in our CI/CD integration. This allows you to automate the discovery and auditing of APIs regardless of the OAS version.
REST API Static Security Testing
- Azure Pipelines
- Bitbucket Pipelines
- Github Actions
- GitLab
- Jenkins
- Generic Docker image
Support in Bamboo and Tekton will come later.
Aside from Jenkins, after upgrading, make sure you update the pipeline configuration to use the latest version of plugin.
For more details on CI/CD integration for the supported CI/CD systems, see Integrate CI/CD solutions with 42Crunch Platform.
Dedicated tab for skipped issues in the audit report
The audit report now has a dedicated tab that lists skipped issues from the audit rules applied to your API. The list includes all issues listed in the audit rules, from both the default and tag-based rules. It does not necessarily mean that these issues were raised in the audit, just that if they had been, they would not be shown in the audit report. This lets you better understand what might have been left out of the audit report.
For more details, see Audit report.
Compatibility
This section lists the compatible Docker images for some of the components of 42Crunch API Security Platform, as well as other possible compatibility details.
API Firewall images
This release is compatible with the following API Firewall images:
- NEW:
42crunch/apifirewall:v1.1.9- Upgrade to
expat 2.7.0-r0(CVE-2024-8176) - Upgrade to
golang.org/x/net 0.36.0(CVE-2025-22870)
- Upgrade to
We highly recommend that you switch to the latest image version to take full advantage of the new features and security improvements.
42crunch/apifirewall:v1.1.8- Upgrade to
openssl-3.3.3(CVE-2024-12797, CVE-2024-13176)
- Upgrade to
42crunch/apifirewall:v1.1.7- Fixed the failure in forwarding large request bodies
- Upgrade to
go-1.23.4(CVE-2024-45338)
-
42crunch/apifirewall:v1.1.6- Upgrade to
openssl-3.3.2-r1(CVE-2024-9143)
- Upgrade to
42crunch/apifirewall:v1.1.5- Switch to the system certificate store to fix certificate authority renewal issue
All previous image versions have been deprecated and are no longer supported.
When you switch the version of the API Firewall image, you must reconfigure any existing protection configurations so that they work with the new version. For more details, see Reconfigure API Protection.
API Scan images
This release is compatible with the following API Scan images for running it on-premises.
Scan v2
- NEW:
42crunch/scand-agent:v2.0.21- Support for OWASP API Security Top 10 2023
- Sub-schemas from
anyOfconstructions excluded from testing - Improved generation of Boolean values in tests
- Upgrade to
golang-jwt/jwt/v5 v5.2.2(CVE-2025-30204) - Upgrade to
go-redis/v9 v9.7.3(CVE-2025-29923) - Upgrade to
kin-openapi v0.131.0(CVE-2025-30153)
We highly recommend that you switch to the latest image version to take full advantage of the new features and security improvements.
42crunch/scand-agent:v2.0.20- Fixed response validation on arrays
- Upgrade to
golang.org/x/net v0.37.0(CVE-2025-22870)
42crunch/scand-agent:v2.0.19- Initial support for the OAS v3.1 in API Scan
- Improved
.p12support - Upgrade to
golang.org/x/oauth2 v0.25.0(CVE-2025-22868) - Upgrade to
golang.org/x/crypto v0.33.0(CVE-2025-22869)
42crunch/scand-agent:v2.0.18- Fixed handling of empty scenario list in the lax scanning mode
- Increased maximum number of items in generated arrays
42crunch/scand-agent:v2.0.17- Upgrade to
go-git v5.13.1(CVE-2025-21613, CVE-2025-21614) - Upgrade to
nanoid v3.3.8(CVE-2024-55565) - Upgrade to
golang.org/x/net v0.33.0(CVE-2024-45338) - Upgrade to
golang.org/x/crypto v0.31.0(CVE-2024-45337)
- Upgrade to
-
42crunch/scand-agent:v2.0.15- Fixed replacement of placeholder texts in variables when generating test requests
- Fixed generation of properties in test requests
- Fixed regression on
nullenums
-
42crunch/scand-agent:v2.0.13- A new property in the scan report to indicate if running a scan test succeeded or not
42crunch/scand-agent:v2.0.12- Fixed scan report timestamp
42crunch/scand-agent:v2.0.11- Upgrade to
Golang v1.23.1(CVE-2022-30635, CVE-2024-34155, CVE-2024-34156, CVE-2024-34158)
- Upgrade to
42crunch/scand-agent:v2.0.10- New test
response-body-badformat-scan - Fixed scan configuration creation when
itemsisnull - Fixed excessive data exposure reporting
- New test
42crunch/scand-agent:v2.0.9- Scan v2 in v1-compatible mode
- Support for
Acceptheaders - Upgrade to
Golang 1.22.5(CVE-2024-24789, CVE-2024-24790, CVE-2024-24791)
42crunch/scand-agent:v2.0.8- New test
path-item-method-not-allowed-no-authn-scan - Support for
apiConnectivityCheck,maxTimeoutRetryAttempts, andrequestHeaderNameRequestType - Fixed implementation of
reportIncludeRequestBodyandreportIncludeResponseBody - Fixed handling of lookahead and lookbehind assertion references in regular expressions
- New test
42crunch/scand-agent:v2.0.7- Upgrade to
Golang 1.22.3(CVE-2020-8559, CVE-2024-24788)
- Upgrade to
42crunch/scand-agent:v2.0.6- Lax testing mode
- Fixed generating conformance test requests when multiple required properties are defined
42crunch/scand-agent:v2.0.4- Numeric values exceeding the limits of
float64presented as strings
- Numeric values exceeding the limits of
42crunch/scand-agent:v2.0.3- Upgrade to
Golang 1.21.5(CVE-2023-45284, CVE-2023-45283, CVE-2023-39326, CVE-2023-45283) - New scan report
- Tests
parameter-header-contenttype-wrong-scanandpartial-security-accepted - Support for
reportIncludeRequestBody,reportIncludeResponseBody,reportMaxRequestSizeHappyPath,reportMaxRequestSizeTest - Improved logging for runtime limit
- Heartbeat check
- Upgrade to
All previous image versions have been deprecated and are no longer supported.
Scan v1
- NEW:
42crunch/scand-agent:v1.22.27- Support for OWASP API Security Top 10 2023
- Sub-schemas from
anyOfconstructions excluded from testing - Improved generation of Boolean values in tests
- Upgrade to
golang-jwt/jwt/v5 v5.2.2(CVE-2025-30204) - Upgrade to
go-redis/v9 v9.7.3(CVE-2025-29923) - Upgrade to
kin-openapi v0.131.0(CVE-2025-30153)
We highly recommend that you switch to the latest image version to take full advantage of the new features and security improvements.
42crunch/scand-agent:v1.22.25- Initial support for the OAS v3.1 in API Scan
- Improved
.p12support - Upgrade to
golang.org/x/oauth2 v0.25.0(CVE-2025-22868) - Upgrade to
golang.org/x/crypto v0.33.0(CVE-2025-22869)
-
42crunch/scand-agent:v1.22.24- Fixed handling of nullable enums and empty strings
- Increased maximum number of items in generated arrays
42crunch/scand-agent:v1.22.23- Upgrade to
go-git v5.13.1(CVE-2025-21613, CVE-2025-21614) - Upgrade to
nanoid v3.3.8(CVE-2024-55565) - Upgrade to
golang.org/x/net v0.33.0(CVE-2024-45338) - Upgrade to
golang.org/x/crypto v0.31.0(CVE-2024-45337)
- Upgrade to
42crunch/scand-agent:v1.22.21- Default value maximum scan report size 20 MB to align with Scan v2
42crunch/scand-agent:v1.22.20- Fixed excessive data exposure reporting
42crunch/scand-agent:v1.22.19- Upgrade to
Golang v1.23.1(CVE-2022-30635, CVE-2024-34155, CVE-2024-34156, CVE-2024-34158) - Happy path tests included in the number of tests
- Upgrade to
42crunch/scand-agent:v1.22.18- Fixed scan configuration creation when
itemsisnull
- Fixed scan configuration creation when
42crunch/scand-agent:v1.22.17- Upgrade to
Golang 1.22.5(CVE-2024-24789, CVE-2024-24790, CVE-2024-24791)
- Upgrade to
42crunch/scand-agent:v1.22.16- Upgrade to
Golang 1.22.3(CVE-2020-8559, CVE-2024-24788)
- Upgrade to
42crunch/scand-agent:v1.22.15- Fixed handling of query parameters in request generation
- Fixed generating conformance test requests when multiple required properties are defined
42crunch/scand-agent:v1.22.14- Upgrade to
Golang 1.21.5(CVE-2023-39326, CVE-2023-45283)
- Upgrade to
42crunch/scand-agent:v1.22.13- Upgrade to
Golang 1.21.3(CVE-2023-45284, CVE-2023-45283) - Heartbeat check to keep the connection to 42Crunch Platform active in case of extremely long scans
- Fixed handling of
exampleandx-42c-sample
- Upgrade to
42crunch/scand-agent:v1.22.12- Support for
text/plainas content type - Support for
read-onlyproperties
- Support for
-
42crunch/scand-agent:v1.22.11- Upgrade to
Golang 1.20.7(CVE-2023-39319, CVE-2023-39318, CVE-2023-3978, CVE-2023-29409) - Fixed handling of
<and>characters in the request payload - Improved handling of content not supported by API Scan
- Upgrade to
42crunch/scand-agent:v1.22.9- Performance improvements to scan configuration generation
- Better memory handling when generating array items of the type
filefor scan requests - Better handling of expired customization rules
- Improved JSON schema validation for UTF-8 strings
42crunch/scand-agent:v1.22.8- Upgrade to
Golang 1.20.4(CVE-2022-41716, CVE-2022-41717, CVE-2022-41720, CVE-2022-41722, CVE-2022-41723, CVE-2022-41724, CVE-2022-41725, CVE-2023-24532, CVE-2023-24534, CVE-2023-24536, CVE-2023-24537, CVE-2023-24538, CVE-2023-24539, CVE-2023-24540, CVE-2023-29400)
- Upgrade to
42crunch/scand-agent:v1.22.7- Updates to regular expression library
42crunch/scand-agent:v1.22.6- Fixed regular expressions handling
In some rare cases, certain regular expression patterns could send the on-premises scan to an infinite loop, and the process would not finish. This image version fixes that, so if you are experiencing on-premises scan hanging, we recommend upgrading from the previous scan images to this one.
- Fixed regular expressions handling
42crunch/scand-agent:v1.22.4- Improved array iteration
All previous image versions have been deprecated and are no longer supported.
Changed behavior
Depending on your API, the following changes in Security Audit may affect your audit results on APIs following the OAS v3.1:
v3_1-validation-property-value-typeis not raised whenexclusiveMinimumandexclusiveMaximumhave numeric values, but with other values (such as boolean) it is raised.v3_1-semantic-unknown-propertyandv3_1-warning-sample-undefinedare no longer raised for the propertyexamplein schemas.
In addition, API Scan no longer runs tests on subschemas found in an anyOf construction, which may affect the number of found issues reported.
Known issues
This release has the following known issues.
OWASP API Security Top 10 2023 not in security quality gates
The OWASP API Security Top 10 vulnerabilities are not yet included as fail-on conditions in security quality gates (SQGs). This will be fixed in the next release.
Manage teams permission not shown on list of users
The permission to manage teams is not yet shown on the list of users in your organization, but you can view all permissions that a user has by clicking the permission column. This permission also does not yet have a shortcut that you could use when searching by permission.
These will be fixed in a future release.
Changing tagging on an API may trigger an unrelated error on the UI
Sometimes applying tags to or removing them from an API may trigger an unrelated error on failing to fetch the SQG approval report for the API. This happens if the API in question has been scanned on-premises and the scan has finished after you arrived on the API Summary page, because the UI cannot find the latest on-premises scan report and the associated approval report. Refreshing the page gets the latest reports and resolves the issue.
Tagging and untagging the API is not affected by this error: tags get correctly applied and removed in any case.
This will be fixed in a future release.
Data dictionary duplication
Duplicating a data dictionary does not yet duplicate the values in it.
This will be fixed in a future release.
Scan customization rules may lead to no response codes being accepted.
In some cases, scan rules can lead to HTTP status response codes in API responses that are normally expected (for example, HTTP 401 or HTTP 404) to be treated as unexpected. This in turn can lead to a false positive in the scan results.
By default, the expected HTTP status response codes that are defined in scan rules applied to the scanned API take preference over the response codes that API Scan would otherwise expect. However, this can cause problems in scan process if your scan rule only skips header or response body analysis but does not define any expected response codes, either for happy path requests or for particular test IDs. This results in the scan rule to have null defined as the expected response code, and because the scan rule takes preference over the default scan behavior, no response codes except null are accepted. This in turn means that some tests are incorrectly flagged as returning unexpected response codes when they were in fact successful.
We are currently investigating the best way how to reconcile the designed behavior of API Scan and scan rules in these cases, and this issue will be fixed in a future release.