42Crunch Platform release, December 15, 2021
This 42Crunch API Security Platform release introduces security quality gates (SQGs), default customization rules for API Security Audit and API Scan, and setting certain tag categories to be mandatory for APIs in your organization. In addition, we have also added new checks in Security Audit for validating regular expression, and improved the scan report.
New features
The following are the new features and improvements to the existing ones in this release.
Security quality gates
Organization administrators can now define SQGs that APIs in their organization must pass.
- Set the baseline for the acceptance criteria on security of that APIs must meet.
- Get assurances that APIs comply to your security standards, or clear indicators when they do not
- Have a clear starting point for what to fix in your API first.
Each organization gets a default SQG out of the box, so that you automatically have an overall quality indicator at your disposal right from the start. Currently, SQGs provide quality criteria for Security Audit, but more criteria will be added in future releases.
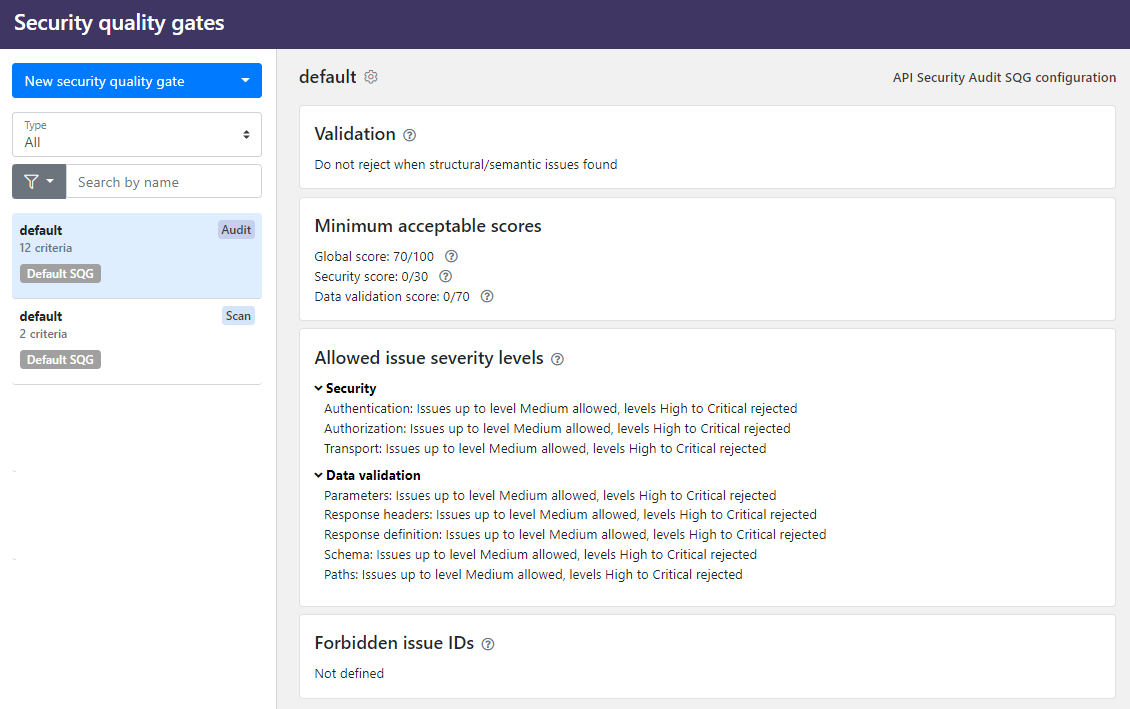
For more details, see Security quality gates.
Default customization rules
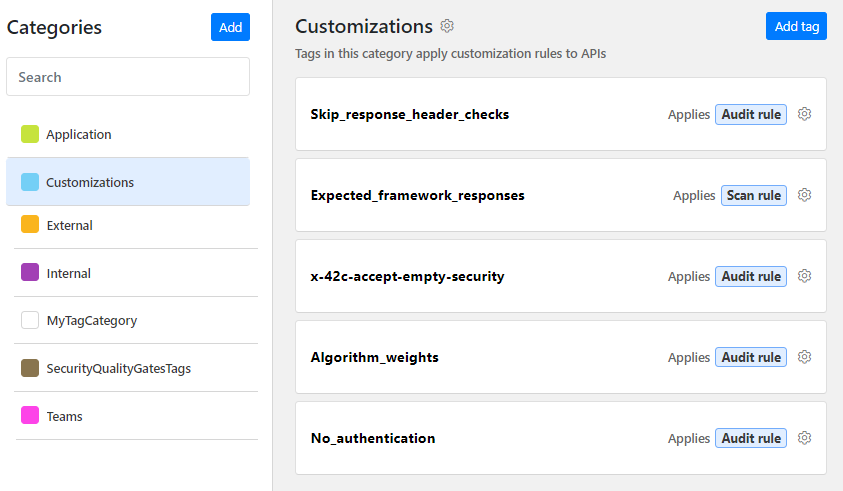
Organization administrators can now define default customization rules that are automatically applied to all APIs in their organization.
- Apply a set of directives for Security Audit and API Scan without the need of tagging an API for the rule.
- Enforce your rules right from the first import of APIs in your organization, even before they get tagged.
- Default rules can be combined with rules applied with tags: lists of directives from the default rule are added on top of the directives from the more specific rule from the tag, on non-list directives the rule from tag takes precedence.
For more details, see Default customization rules.
To help you get started, we have added a default rule for audit and scan in your organization, and you can edit them as you like. To help to keep you organized, we have added predefined categories (which again you can edit as needed) so you have a place where to put all your customization rules and SQGs.
Mandatory tag categories
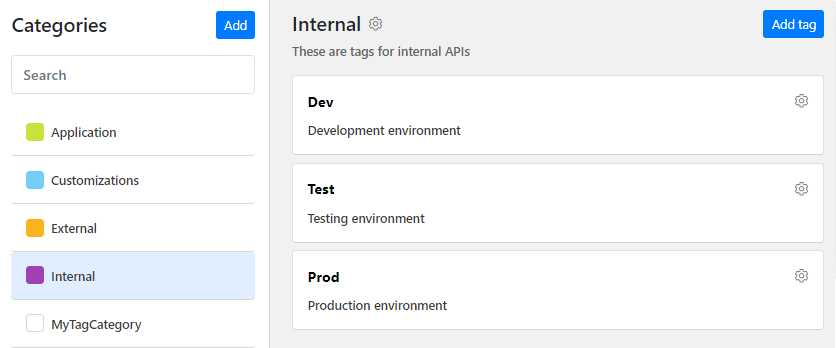
Organization administrators can now define certain type of tags to be mandatory on APIs throughout in their organization.
- Add a directive in customization rules that sets which tag categories are mandatory for APIs in your organization.
- All APIs must have at least one tag applied to them from each mandatory tag category.
- Define mandatory tag categories in your default audit rule to automatically alert developers on how they must tag their API definitions as soon as they are imported in 42Crunch Platform.
For more details, see Customizations for mandatory tag categories.
In addition, all tags now show their dependencies, meaning which SQGs or customization rules they apply.
New vendor extension and checks to Security Audit
Security Audit now offers a new vendor extension to the OpenAPI Specification (OAS), x-42c-mtls, that you can add in API operations — or globally for the whole API — that use mutual TLS authentication, so that the algorithm can take this added security into account when calculating the audit score. For more details, see x-42c-mtls.
We have added new checks for checking if a regular expression conflicts with the minLength or maxLength defined for a string object. Depending on your API definition, this may affect your audit score. For more details, see the following:
- For OAS v2:
- Pattern of the string parameter does not match the 'minLength' or 'maxLength' properties
- Pattern of the string header does not match the 'minLength' or 'maxLength' properties
- Pattern of the string schema does not match the 'minLength' or 'maxLength' properties
- For OAS v3:
- Pattern of the string schema does not match the 'minLength' or 'maxLength' properties
There are also new checks to check that regular expressions are valid Perl Compatible Regular Expressions (PCREs):
- OAS v2: Pattern is not a valid PCRE regular expression
- OAS v3: Pattern is not a valid PCRE regular expression
These checks do not affect your audit score.
To alert on missing tags from mandatory tag categories, we have added the following checks:
- OAS v2: Mandatory tag category not applied to the API
- OAS v3: Mandatory tag category not applied to the API
These checks do not affect your audit score but are treated like the API was not a structurally valid OpenAPI definition, which in turn prevents proceeding with the API in 42Crunch Platform and provides a clear incentive to ensure all required tags are applied in timely fashion.
In addition, we have fixed a bug where Security Audit did not correctly follow references defined for a schema discriminator.
New view in executive dashboard
The executive dashboard for organization administrators now offers an executive summary for Security Audit:
- Get at-a-glance view on the quality of APIs in your organization and are they meeting the criteria set out in your SQGs.
- See a summary on the severity of security issues found hiding in the API definitions.
- Export the summary as a PDF to share other stakeholders or interested parties outside 42Crunch Platform.
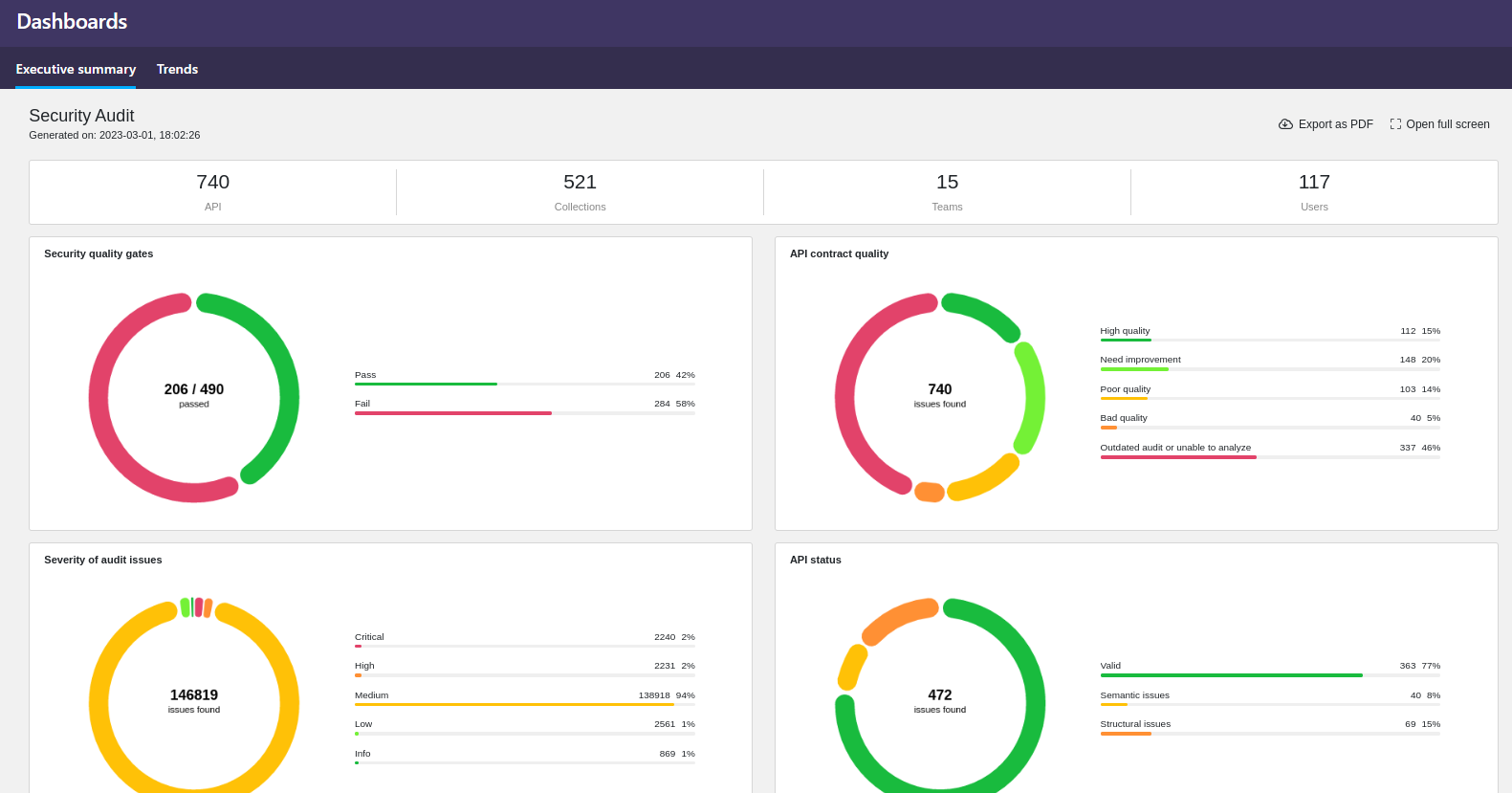
The charts for the trends in Security Audit, API Scan, and API Protection for your APIs are still available on the second tab. For more details, see Executive dashboard.
Improved scan report in API Scan
Scan report now shows more details on the test in a scan than before.
- A visual summary on passed and failed happy path requests now included alongside the summary of the test requests.
- Clearer separation between the two parts of response analysis in the scan:
- Error handling and the received HTTP status code: Did the API response match what API Scan expected or not, or — in the worse case — did the intentionally malformed request not raise an error at all.
- Analysis of the response content: Even API responses that match what API Scan expected for the sent request could uncover discrepancies between the API contract and its backend implementation, meaning that successful test status does not guarantee there are no problems.
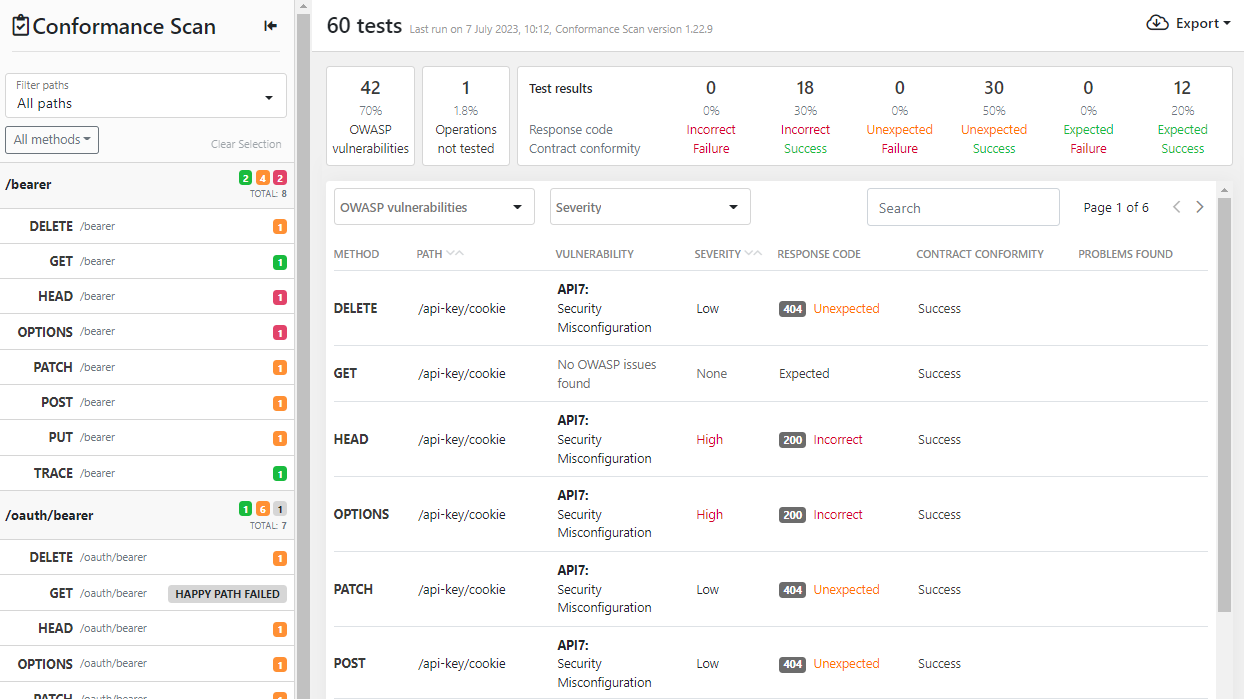
Because of the significant changes in the report format, you must rerun API Scan to view the scan report of a previously scanned API. The changes also mean that only the latest Docker image for on-premises scan is fully compatible with the platform UI (see API Scan images).
If you are running API Scan on-premises, you can also add the environment variable REPORT_FULL to the Docker command to change what is included in the scan report.
Customization rules for API Scan now support skipping specific operations (methods) in scans. See Customizations for API Scan.
In addition, we have fixed the following bugs:
- Generating scan configuration now properly handles JSON numbers for schemas of the type
integerornumber. - String generator in API Scan now properly handles
\band other ASCII character classes. - The test ID
partial-security-acceptedis now included in scan customization rules.
New protections for API Firewall
We have introduced two new protections that you can apply directly to your OpenAPI definitions to instruct API Firewall how it should protect these APIs:
- Client IP address override: This protection lets you direct API Firewall to take the value for
client.ipfrom a message header rather than simply use the IP address from where the API call arrived to API Firewall. This is particularly useful if API traffic passes through internal components that could change the original client IP address to an internal IP address before the call reaches API Firewall. - Access control based on IP address range: This protection lets you define allowlists of IP addresses or address ranges that are allowed to make API calls. API Firewall blocks calls from addresses that are not on the list.
These protections require API Firewall image v1.0.12 (or higher).
For more details on protections in general, see Protections and security extensions.
Transferring API collection ownership
You can now change the owner of your API collections to another user and give them the full control over it. See Change the owner of an API collection.
In addition, when organization administrators delete a user account, for example, because the user has left the company, they must transfer all assets related to that user account to someone else before they can delete the account. For more details, see Delete a user account.
Compatibility
This section lists the compatible Docker images for some of the features of 42Crunch API Security Platform, as well as other possible compatibility details.
API Firewall images
This release is compatible with the following API Firewall images:
42crunch/apifirewall:v1.0.12- Support for
x-42c-access-control-based-on-ip-range_0.1andx-42c-set-client-ip_0.1. - Improved matching to allow filtering API calls by IP or network addresses.
- Fixed setting the request path when
$TARGET_URLcontains a basepath. - Upgrade to Apache
httpd2.4.51 (CVE-2021-42013).
- Support for
42crunch/apifirewall:v1.0.11GUARDIAN_BLOCKING_LEVELandGUARDIAN_DEFAULT_API_BLOCKING_LEVELenvironment variables.- Upgrade to Apache
httpd2.4.50 (CVE-2021-41524, CVE-2021-41773).
42crunch/apifirewall:v1.0.10- Fixed cookie attribute parsing in responses.
- Upgrade to Apache
httpd2.4.48 (CVE-2021-33193, CVE-2021-34798, CVE-2021-36160, CVE-2021-39275, CVE-2021-40438). - Updated platform CA chain.
42crunch/apifirewall:v1.0.9-1- Fixed handling
UTF-8patterns in JSON schemas. - Upgrade to
openSSL-1.1.1l(CVE-2021-3711, CVE-2021-3712). - Updated platform CA chain.
- Fixed handling
All previous image versions have been deprecated and are not compatible with this version of the platform.
When you switch the version of the API Firewall image, you must reconfigure any existing protection configurations so that they work with the new version. For more details, see Reconfigure API Protection.
API Scan images
This release is compatible with the following API Scan images for running it on-premises:
42crunch/scand-agent:v1.14.1- Improvements to scan report.
- New environment variable
REPORT_FULLfor scan report. - Skipping operations (methods) with customization rules.
- Generating scan configuration now properly handles JSON numbers for schemas of the type
integerornumber. - String generator in API Scan now properly handles
\band other ASCII character classes. - Upgraded Golang
crypto/sshcomponent (CVE-2020-29652).
Known issues
This release has the following known issues.
Security quality gates shown also for community users
The menu item for SQGs is erroneously shown in the main menu of 42Crunch Platform even on accounts that belong to the free Community organization. However, SQGs are only available for business users, not in the Community organization, so the menu item does not do anything.
We are working to fix this as soon as possible.
Transferring users' assets also shown when deleting user accounts with no assets
When you delete a user account, you must choose a new owner for assets related to that account, even when the account in question has no assets to transfer at all. In effect, this means that you select a new owner, but there is nothing to transfer to them. The user account is successfully deleted.
This will be fixed in a future release.
Self-registration email template not rendering properly in Yahoo! mail
The notification email sent to you when you self-register a user account to 42Crunch Platform is currently not rendered properly in Yahoo! mail. Other common email providers are not affected.
We are investigating the issue and hope to fix it as soon as possible.
Promoting organization administrators resets sharing permissions
Currently, if you promote new organization administrators, their permissions to share API collections are automatically reset to sharing only with named teams and users. If you want to allow the new organization administrators to share with everyone in your organization again, you must re-enable it in the user permissions. The permissions of existing organization administrators are not affected.
This will be fixed in a future release.
Automatic sharing with everyone not possible for new SSO users
Currently, the sharing permissions for new users onboarded to 42Crunch Platform through single sing-on (SSO) integration are automatically set to sharing only with named teams and users. If you want to allow the users to share with everyone in your organization, you must enable it in the user permissions. The permissions of existing users in your organization have been retained as they were.
This will be fixed in a future release.
API Scan string limits may conflict with minLength or maxLength values
By default, API Scan limits the maximum length for strings in the requests it sends during the scan to 4096. If the properties minLength or maxLength or the length limits in a regular expression that you have defined for an API operation in your API definition conflict with this limit, it causes issues during the scan.
If the minimum length required is longer than the string length limit allowed in API Scan, the scan cannot create the happy path request for that operation to establish a baseline. If the maximum length allowed in the API is longer than the allowed string length limit in API Scan, the scan can create the happy path request but not the actual request during the scan.
In both cases, the operation is shown as a skipped operation in the scan report, but for different reasons. You must fix the operation in your API definition before it can be successfully scanned.
Regular expression lookaheads may cause issues
If your API definition has regular expressions with either positive or negative lookaheads defined, these may cause weird behavior, for example, in API Scan.