42Crunch Platform release, November 9, 2021
This 42Crunch API Security Platform release introduces improved scan report and OpenID Connect (OIDC) support in API Scan, and lets you update tag category settings and customization rules.
New features
The following are the new features and improvements to the existing ones in this release.
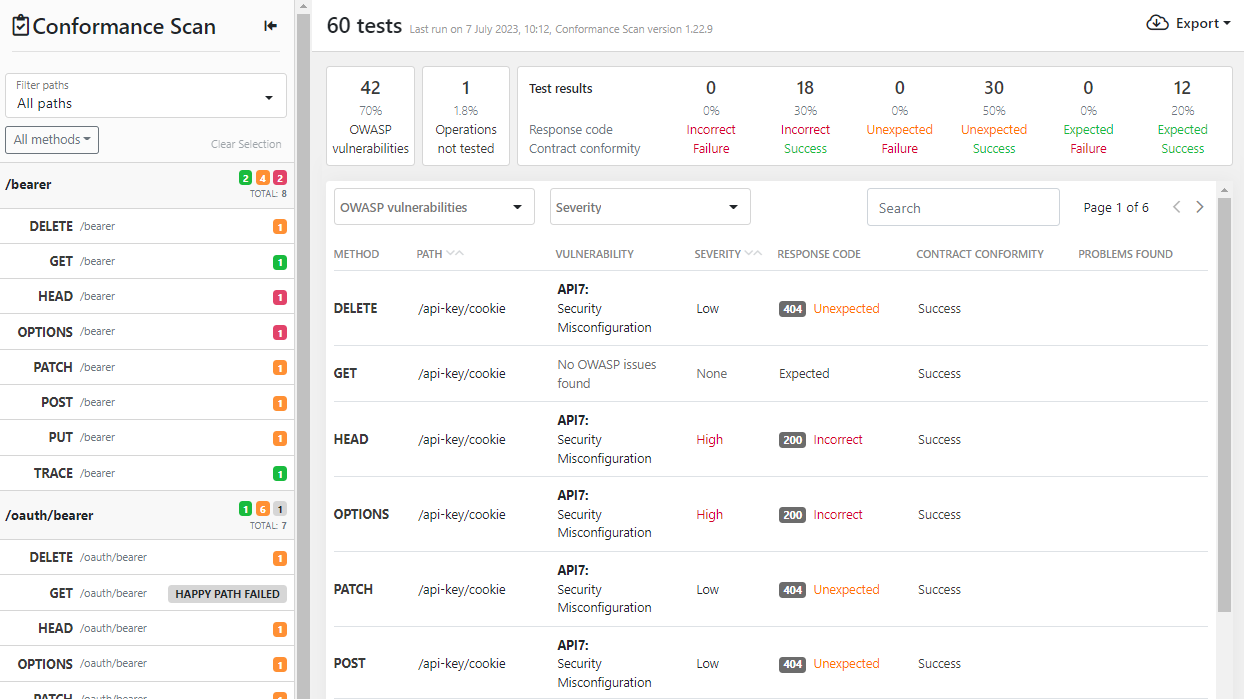
Improved scan report in API Scan
The scan report has been restructured for better clarity. The report now shows all tests that the scan did, their status (did the API pass or fail the test), and the problems that each test found.
API Scan now supports configuring the details for OIDC authentication when scanning APIs that follow the OpenAPI Specification (OAS) v2. In addition, configuring the authentication is now context-sensitive, meaning that the scan configuration wizard only shows you the authentication methods defined and used in your API definition. For added security, sensitive authentication details, such as the header or cookie values for API keys, are hidden by default when you enter them on the UI.
We have also included more information on logs and where you can choose to write them when running API Scan on-premises. We have also changed the syntax of the filename for logs to ensure they do not get overwritten by subsequent scans if you choose to write them in a file. For more details, see Scan logs.
In addition, we have fixed the following bugs:
- API Scan now accepts free-form
additionalPropertiesfields (additionalProperties: {}) in dictionary and map definitions in the scanned APIs. - API Scan now properly indicates that testing is incomplete if no issues were found but some operations could not be tested because the happy path request failed.
- The descriptions on failed happy path requests have been improved.
API Firewall log strategy for transaction log handling
You can now use the API-specific environment variable LOG_STRATEGY to define what API Firewall does if you have set it to send logs to 42Crunch Platform but the instance loses the platform connection.
For more details, see Stop API Firewall from serving traffic without logs.
In addition, we have also improved how API Firewall handles the environment variable TARGET_URL in host mapping, and API calls can now be filtered by IP or network addresses.
Update tag category settings
Organization administrators can now update the settings of the tag categories, such as allow users to add new tags or allow adding multiple tags from a category.
If you decide to allow applying multiple tags from a category, you cannot change your mind and switch it off later. Users might already have applied multiple tags from the category to their APIs and it would not be possible to automatically decide how to roll back in these cases. It is best to delete the category and start again, this time not allowing multiple tags. You can always decide to allow multiple tags later but once you do, you cannot change back.
For more details, see Create new tags and categories.
Update and copy customizations rules
Organization administrators can now update audit and scan rules they have created to tweak them for a better fit after testing their impact in action.
Creating new rules is faster, too: you can now copy an existing rule as your starting point, so you do not have to fill in all details from scratch every time. In addition, the expiration date for new audit and scan rules is no longer set unless you specifically define one.
For more details, see Customize platform features.
Improvements to Security Audit
We have fixed a bug in how Security Audit imported and analyzed referenced schemas that could cause issues with allOf. Security Audit now first imports all referenced schemas before it starts assessing them. Depending on your API definition, this may affect your audit score.
In addition, we have fixed a mapping issue with the encyclopedia articles and issue IDs for the checks validation-global-securityrequirement-unreferenced and validation-operation-securityrequirement-unreferenced, so that the articles for these checks are properly shown.
Improvements to showing API collections sharing
Previously, in some cases the list of users that an API collection was shared with could show empty on the platform UI even though in reality the collection had been shared. We have now fixed this issue and the sharing is shown properly on the UI.
Compatibility
This section lists the compatible Docker images for some of the features of 42Crunch API Security Platform, as well as other possible compatibility details.
API Firewall images
This release is compatible with the following API Firewall images:
42crunch/apifirewall:v1.0.12- Improved matching to allow filtering API calls by IP or network addresses.
- Fixed setting the request path when
$TARGET_URLcontains a basepath. - Upgrade to Apache
httpd2.4.51 (CVE-2021-42013).
42crunch/apifirewall:v1.0.11GUARDIAN_BLOCKING_LEVELandGUARDIAN_DEFAULT_API_BLOCKING_LEVELenvironment variables.- Upgrade to Apache
httpd2.4.50 (CVE-2021-41524, CVE-2021-41773).
42crunch/apifirewall:v1.0.10- Fixed cookie attribute parsing in responses.
- Upgrade to Apache
httpd2.4.48 (CVE-2021-33193, CVE-2021-34798, CVE-2021-36160, CVE-2021-39275, CVE-2021-40438). - Updated platform CA chain.
42crunch/apifirewall:v1.0.9-1- Fixed handling
UTF-8patterns in JSON schemas. - Upgrade to
openSSL-1.1.1l(CVE-2021-3711, CVE-2021-3712). - Updated platform CA chain.
- Fixed handling
42crunch/apifirewall:v1.0.8-1- Fixed the parsing of array parameters with OASv2 when no
collectionFormatis specified. - Fixed sending transaction logs to the platform when log destination is set to
PLATFORM+STDOUT. - Updated platform CA chain.
- Fixed the parsing of array parameters with OASv2 when no
All previous image versions have been deprecated and are not compatible with this version of the platform.
When you switch the version of the API Firewall image, you must reconfigure any existing protection configurations so that they work with the new version. For more details, see Reconfigure API Protection.
API Scan images
This release is compatible with the following API Scan images for running it on-premises:
42crunch/scand-agent:v1.13.0- Updated scan report structure.
- Improved happy path status.
- Free-form
additionalPropertiesaccepted in dictionary and map definitions. - Changed log filename syntax to
<task ID>-<epoch timestamp>-scand.log. - Log level specified in a Docker command now overrides the log level defined in the scan configuration.
42crunch/scand-agent:v1.12.2- Customization with scan rules.
- Fixed a bug in creating string values where the default value could conflict with set
maxLength. - Results from scans reflected in the executive dashboards in 42Crunch Platform.
42crunch/scand-agent:v1.11.1- Fixed a bug in scan occasionally generating a
nullbody - Fixed a bug in the injection
schema-uniqueitems-unique-scan. - Support for
nullvalues for the extensionx-42c-sample.
- Fixed a bug in scan occasionally generating a
42crunch/scand-agent:v1.10.0- Fixed bug with default request timeout.
42crunch/scand-agent:v1.9.4- Fixed serialization of array objects in query string parameters.
- Changed behavior in log upload.
42crunch/scand-agent:v1.8.6- Fixed happy path request generation with the value from
defaultorx-42c-sample.
- Fixed happy path request generation with the value from
42crunch/scand-agent:v1.8.3- Removed the unnecessary JSON complexity check.
- Scan configurations can be pushed with API key in addition to session ID.
42crunch/scand-agent:v1.8.1- Improved JSON schema library.
- Improved messages.
- Case-insensitive header name evaluation.
- Option to reuse values sent during the happy path requests as a basic example (can cause problems if the API has some value constraints, like unique ID, email, or name, as the scan could be unable to generate a value for a really specific case).
42crunch/scand-agent:v1.7.4- Fixed handling of
multipleOfwhen its range is[0;0.50].
- Fixed handling of
42crunch/scand-agent:v1.6.0- This version replaces
42crunch/scand-agent:v1.5.2-bugfix01. - Environment variables for communication through proxy to both platform and APIs.
- Scan handles
nullvalue in API response.
- This version replaces
42crunch/scand-agent:v1.5.1- New test
partial_security_acceptedfor testing how missing security requirements are handled. - TLS configuration allows a remote server to repeatedly request renegotiation.
- Improved handling of slashes (
/) and wildcards likeapplication/*in test requests and JSON encoder. - Masked credentials and other small improvements in scan logs.
- More details shown when a happy path request fails
- Improved generation of strings, numbers, integers, and arrays.
- Support for proxy configuration.
- New test
Known issues
This release has the following known issues.
Skipped HTTP methods not excluded from API Scan
Excluding HTTP methods from the scan tests in a scan rule is not yet working: the scan still generates tests for these HTTP methods.
This will be fixed in a future release.
Promoting organization administrators resets sharing permissions
Currently, if you promote new organization administrators, their permissions to share API collections are automatically reset to sharing only with named teams and users. If you want to allow the new organization administrators to share with everyone in your organization again, you must re-enable it in the user permissions. The permissions of existing organization administrators are not affected.
This will be fixed in a future release.
Automatic sharing with everyone not possible for new SSO users
Currently, the sharing permissions for new users onboarded to 42Crunch Platform through single sing-on (SSO) integration are automatically set to sharing only with named teams and users. If you want to allow the users to share with everyone in your organization, you must enable it in the user permissions. The permissions of existing users in your organization have been retained as they were.
This will be fixed in a future release.
API Scan string limits may conflict with minLength or maxLength values
By default, API Scan limits the maximum length for strings in the requests it sends during the scan to 4096. If the properties minLength or maxLength or the length limits in a regular expression that you have defined for an API operation in your API definition conflict with this limit, it causes issues during the scan.
If the minimum length required is longer than the string length limit allowed in API Scan, the scan cannot create the happy path request for that operation to establish a baseline. If the maximum length allowed in the API is longer than the allowed string length limit in API Scan, the scan can create the happy path request but not the actual request during the scan.
In both cases, the operation is shown as a skipped operation in the scan report, but for different reasons. You must fix the operation in your API definition before it can be successfully scanned.
Regular expression lookaheads may cause issues
If your API definition has regular expressions with either positive or negative lookaheads defined, these may cause weird behavior, for example, in API Scan.