42Crunch Platform release, April 16, 2024
|
Platform version: v1.33.x |
This 42Crunch API Security Platform release brings more support for new users on getting started with the platform features, a new testing mode for API Conformance Scan (v2 only), and several UX improvements.
New features
The following are the new features and improvements to the existing ones in this release.
More support for new users to 42Crunch Platform
Knowing where to start with something new can sometimes be daunting. That is why we have introduced more support on getting started with our platform:
- Get suggestions on what to do first, whether you are a regular user or organization administrator.
- Check out the tutorial videos on the tasks, and find more related details in the docs easily.
- See basic statistics, like how many APIs or users you have, and use the quick action buttons to jump to the action.
You can leave the tutorials any time you want and take them up again later from where you left off. The tutorials stay available even after completing the whole flow, in case you need to refresh your memory later.
New testing mode for Conformance Scan
This applies to Scan v2 only.
You can now choose how Conformance Scan handles failed happy path requests:
- In the normal testing mode, any operations where the happy path request fails are skipped in the scan, because Conformance Scan could not establish a reliable baseline against which to compare the scan results. This is the recommended mode.
- In the new lax testing mode, Conformance Scan runs the conformance requests even on operations where happy path requests failed. This provides you much more results in your scans, but without establishing the baseline they may not be as reliable.
You can see in the scan report which scan mode was used.
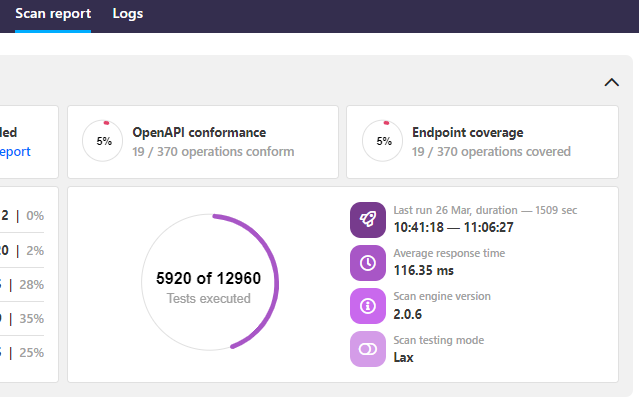
Lax scan testing mode is only supported in the Scan v2 Docker image v2.0.6 or higher. For more details, see Lax testing mode.
On scan report we have also improved the search and filtering of the found issues, and clarified the issue descriptions.
Improvements to Scan v1
On Scan v1, we have fixed how the scan handles query parameters in request generation. Previously, if type was not defined, the properties property was not taken into account when generating the request and query parameters were not included in the request. Now, the scan correctly includes the query parameters in the requests it sends.
Improvements to both Scan v1 and Scan v2
We have fixed a bug in generating conformance test requests for testing how the API implementation handles missing required properties. Previously, if the API defined multiple properties as required, when the scan generated the test request, it accidentally omitted all required properties, not just one of them. Now, omitting required properties is more granular, to ensure the conformance tests can test the right thing.
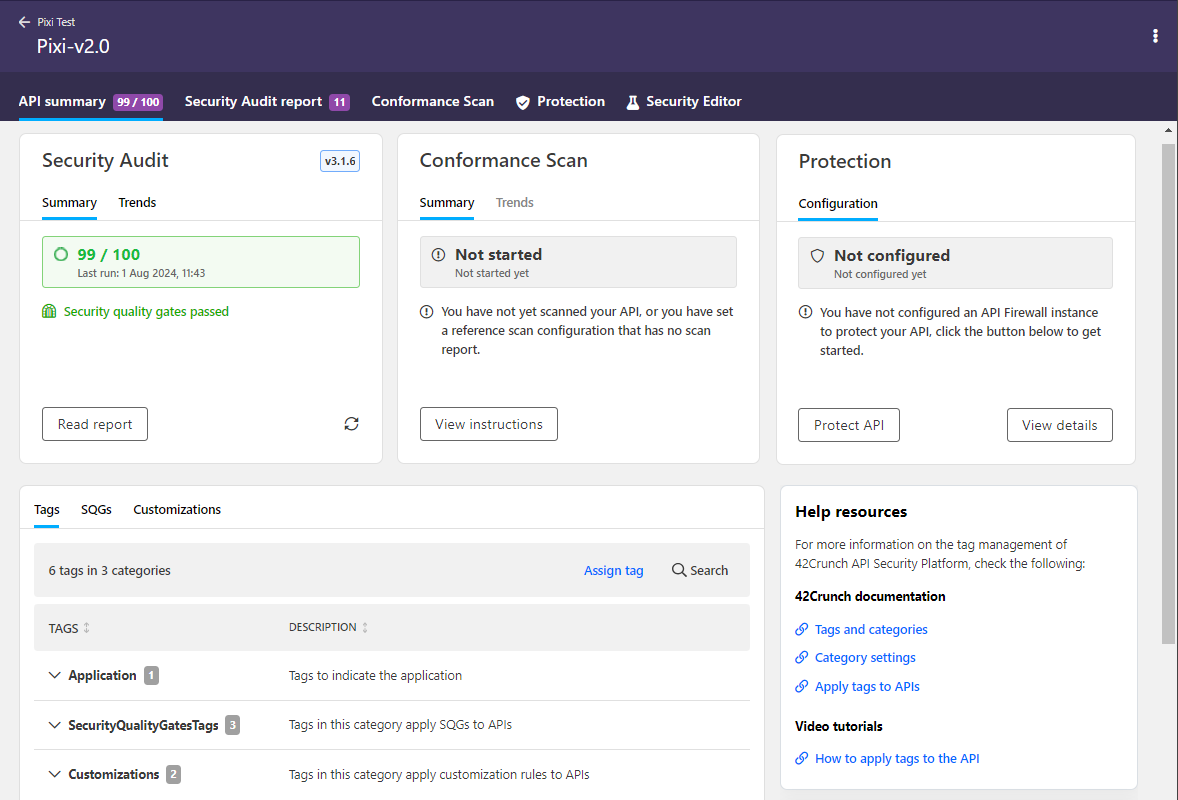
New fresh look for the API summary page
The API summary tab has gotten a new modern look and feel:
- Take in the summary at a glance with less visual clutter.
- Get to API details quicker, with the trend charts now moved onto a dedicated tab on tiles.
- See new details — such as the change in issues per severity level — on the trends tab.
Better handling of query parameters in API Firewall
We have improved how API Firewall handles query parameters: previously, API Firewall assumed query parameter to be required by default, so unless your API specifically stated "required": false on a query parameter, the firewall treated like it was required. Now, API Firewall correctly assumes query parameters not to be required by default.
UX improvements
This release also brings several UX improvements throughout the platform:
- Improvements to security quality gates:
- More structure to the configuration flow, so that it is easier to find the right criteria.
- The impact from each criteria are now clearly spelled out.
- The severity level slider for found issues now more clearly states what is being allowed.
- If you hover on the issue IDs in the drop-down lists, you see the title of the issue.
- Improvements to customization rules:
- More structure to the configuration flow.
- If you hover on the issue IDs in the drop-down lists, you see the title of the issue.
- In scan rules, happy path requests and conformance test requests are now separated, so it is easier to keep track of them.
- When creating new scan rules, the response codes that Conformance Scan expects by default are now pre-filled so you do not have to manually enter them.
- Search: You can now use search to find the SQG, customization rule, data dictionary, or tag category that you are looking for.
- Platform version on the UI: The version of the platform is now shown on the UI, under the list of recent API collections in the main menu. As the platform version is now also included in these release notes, this makes it easier for you to keep track of new features and improvements available to you.
- Persisted login type: The platform now remembers which login type (local account or SSO) you used and automatically directs you to the same one the next time you log in.
Compatibility
This section lists the compatible Docker images for some of the components of 42Crunch API Security Platform, as well as other possible compatibility details.
API Firewall images
This release is compatible with the following API Firewall images:
-
42crunch/apifirewall:v1.1.1- Upgrade to
httpd-2.4.59(CVE-2023-38709, CVE-2024-24795, CVE-2024-27316, CVE-2023-45802, CVE-2023-43622) - Upgrade to
openssl-3.1.6(CVE-2024-2511, CVE-2023-5678, CVE-2024-0727) - Support for the custom blocking mode (a new feature coming in the next release
v1.34) - Fixed handling of query parameters when the property
requiredis not explicitly defined
- Upgrade to
We highly recommend that you switch to the latest version to take the full advantage of the new features and security improvements.
42crunch/apifirewall:v1.0.25- Upgrade to
go-1.21.1(CVE-2023-39319, CVE-2023-39318, CVE-2023-3978, CVE-2023-29409) - Upgrade to
openssl-1.1.1w(CVE-2023-4807, CVE-2023-3817, CVE-2023-3446)
- Upgrade to
42crunch/apifirewall:v1.0.24- Upgrade to
httpd-2.4.57(CVE-2023-25690, CVE-2023-27522) - Upgrade to
openssl-1.1.1u(CVE-2023-2650, CVE-2023-0465, CVE-2023-0466, CVE-2023-0464) - Support for multiple API key security schemes with the same name
- Fixed the handling of content
media-typedeclared as opaque string in response validation - Fixed request body handling when API Firewall is set to non-blocking mode.
- Obfuscated headers (except
Host) in transaction logs when the targeted API is unknown - New versions of JWT validation protections (
x-42c-jwt-validation-ec_0.2,x-42c-jwt-validation-rsa_0.2,x-42c-jwt-validation-hmac_0.2)- Validating the
scopeclaim of OAuth2 JWT tokens - Connecting to the JWKS server through a remote forward proxy
- Validating the
- Upgrade to
42crunch/apifirewall:v1.0.23- Health check over SSL
- The environment variable
PLATFORM_HOST - Fixed the handling of
multipart/form-datarequests - Upgrade to
openssl-1.1.1t - Upgrade to
httpd-2.5.55 -
Upgrade to
apr-util-1.6.3
42crunch/apifirewall:v1.0.22- Fixed JWT signature validation
- Allowed plain string content definition
- Upgrade to
openssl-1.1.1s - Upgrade to
libexpat 2.5.0 - Upgrade to
libapreq 2.17 - Upgrade to
libjansson 2.14 - Upgrade to
libjose 11 - Upgrade to
libmaxminddb 1.7.1
42crunch/apifirewall:v1.0.21- Fixed
contenthandling in non-body parameters - HTTP status response code synchronization with Conformance Scan default expectations
- Fixed
42crunch/apifirewall:v1.0.20- Upgrade to
openssl-1.1.1o(CVE-2022-2274, CVE-2022-2097) - Fixed decreasing the number of active instances when firewall shuts down abruptly
- Upgrade to
42crunch/apifirewall:v1.0.19- Upgrade to
httpd-2.4.54(CVE-2022-26377, CVE-2022-28330, CVE-2022-28614, CVE-2022-28615, CVE-2022-29404, CVE-2022-30522, CVE-2022-30556, CVE-2022-31813)
- Upgrade to
42crunch/apifirewall:v1.0.18- Upgrade to
openssl-1.1.1o(CVE-2022-0778, CVE-2022-1292, CVE-2022-1343, CVE-2022-1434, CVE-2022-1473) - Proper handling of the properties
readOnlyandwriteOnlyfrom the OpenAPI Specification (OAS) in schemas
- Upgrade to
All previous image versions have been deprecated and are no longer supported.
When you switch the version of the API Firewall image, you must reconfigure any existing protection configurations so that they work with the new version. For more details, see Reconfigure API Protection.
Conformance Scan images
This release is compatible with the following Conformance Scan images for running it on-premises.
Scan v2
42crunch/scand-agent:v2.0.7- Upgrade to
Golang 1.22.3(CVE-2020-8559, CVE-2024-24788)
- Upgrade to
42crunch/scand-agent:v2.0.6- Lax testing mode
- Fixed generating conformance test requests when multiple required properties are defined
We highly recommend that you switch to the latest version to take the full advantage of the new features and security improvements.
42crunch/scand-agent:v2.0.4- Numeric values exceeding the limits of
float64presented as strings
- Numeric values exceeding the limits of
42crunch/scand-agent:v2.0.3- Upgrade to
Golang 1.21.5(CVE-2023-45284, CVE-2023-45283, CVE-2023-39326, CVE-2023-45283) - New scan report
- Tests
parameter-header-contenttype-wrong-scanandpartial-security-accepted - Support for
reportIncludeRequestBody,reportIncludeResponseBody,reportMaxRequestSizeHappyPath,reportMaxRequestSizeTest - Improved logging for runtime limit
- Heartbeat check
- Upgrade to
All previous image versions have been deprecated and are no longer supported.
Scan v1
42crunch/scand-agent:v1.22.16- Upgrade to
Golang 1.22.3(CVE-2020-8559, CVE-2024-24788)
- Upgrade to
42crunch/scand-agent:v1.22.15- Fixed handling of query parameters in request generation
- Fixed generating conformance test requests when multiple required properties are defined
We highly recommend that you switch to the latest version to take the full advantage of the new features and security improvements.
42crunch/scand-agent:v1.22.14- Upgrade to
Golang 1.21.5(CVE-2023-39326, CVE-2023-45283)
- Upgrade to
42crunch/scand-agent:v1.22.13- Upgrade to
Golang 1.21.3(CVE-2023-45284, CVE-2023-45283) - Heartbeat check to keep the connection to 42Crunch Platform active in case of extremely long scans
- Fixed handling of
exampleandx-42c-sample
- Upgrade to
42crunch/scand-agent:v1.22.12- Support for
text/plainas content type - Support for
read-onlyproperties
- Support for
-
42crunch/scand-agent:v1.22.11- Upgrade to
Golang 1.20.7(CVE-2023-39319, CVE-2023-39318, CVE-2023-3978, CVE-2023-29409) - Fixed handling of
<and>characters in the request payload - Improved handling of content not supported by Conformance Scan
- Upgrade to
42crunch/scand-agent:v1.22.9- Performance improvements to scan configuration generation
- Better memory handling when generating array items of the type
filefor scan requests - Better handling of expired customization rules
- Improved JSON schema validation for UTF-8 strings
42crunch/scand-agent:v1.22.8- Upgrade to
Golang 1.20.4(CVE-2022-41716, CVE-2022-41717, CVE-2022-41720, CVE-2022-41722, CVE-2022-41723, CVE-2022-41724, CVE-2022-41725, CVE-2023-24532, CVE-2023-24534, CVE-2023-24536, CVE-2023-24537, CVE-2023-24538, CVE-2023-24539, CVE-2023-24540, CVE-2023-29400)
- Upgrade to
42crunch/scand-agent:v1.22.7- Updates to regular expression library
42crunch/scand-agent:v1.22.6- Fixed regular expressions handling
In some rare cases, certain regular expression patterns could send the on-premises scan to an infinite loop, and the process would not finish. This image version fixes that, so if you are experiencing on-premises scan hanging, we recommend upgrading from the previous scan images to this one.
- Fixed regular expressions handling
42crunch/scand-agent:v1.22.4- Improved array iteration
All previous image versions have been deprecated and are no longer supported.
Deprecated components
The following have been deprecated and will be removed in the future.
Deprecated Conformance Scan images
The following versions of the 42crunch/scand-agent Docker image have been deprecated and will be removed in October 2024:
42crunch/scand-agent:v2.0.242crunch/scand-agent:v2.0.142crunch/scand-agent:v2.0.0
These Conformance Scan images fail to properly validate the property for lax scan testing mode and will not run if that is present in the scan configuration. This is not a problem in existing scan configurations which do not include lax testing mode, but if you reconfigure the scan configuration, the property is included by default. If you are unable to move to a newer scan image version, you can manually remove the property laxTestingModeEnabled from the scan configuration to be able to run the scan. However, we do recommend moving to a newer image version as soon as possible.
See Deprecated API Conformance Scan images.
Known issues
This release has the following known issues.
Only reference scan configuration shows SQG status in the scan report
Currently, the scan report summary shows the SQG status for only on the report of the reference scan configuration. When viewing other reports, the scan summary incorrectly shows that the API would not have any SQGs applied to it. However, SQGs are still being correctly applied and the SQG status correctly shown for each report in the list of scan reports.
This will be fixed in a future release.
Manage teams permission not shown on list of users
The permission to manage teams is not yet shown on the list of users in your organization, but you can view all permissions that a user has by clicking the permission column. This permission also does not yet have a shortcut that you could use when searching by permission.
These will be fixed in a future release.
Changing tagging on an API may trigger an unrelated error on the UI
Sometimes applying tags to or removing them from an API may trigger an unrelated error on failing to fetch the SQG approval report for the API. This happens if the API in question has been scanned on-premises and the scan has finished after you arrived on the API Summary page, because the UI cannot find the latest on-premises scan report and the associated approval report. Refreshing the page gets the latest reports and resolves the issue.
Tagging and untagging the API is not affected by this error: tags get correctly applied and removed in any case.
This will be fixed in a future release.
Data dictionary duplication
Duplicating a data dictionary does not yet duplicate the values in it.
This will be fixed in a future release.
Scan customization rules may lead to no response codes being accepted.
In some cases, scan rules can lead to HTTP status response codes in API responses that are normally expected (for example, HTTP 401 or HTTP 404) to be treated as unexpected. This in turn can lead to a false positive in the scan results.
By default, the expected HTTP status response codes that are defined in scan rules applied to the scanned API take preference over the response codes that Conformance Scan would otherwise expect. However, this can cause problems in scan process if your scan rule only skips header or response body analysis but does not define any expected response codes, either for happy path requests or for particular test IDs. This results in the scan rule to have null defined as the expected response code, and because the scan rule takes preference over the default scan behavior, no response codes except null are accepted. This in turn means that some tests are incorrectly flagged as returning unexpected response codes when they were in fact successful.
We are currently investigating the best way how to reconcile the designed behavior of Conformance Scan and scan rules in these cases, and this issue will be fixed in a future release.