42Crunch Platform release, August 20, 2024
|
Platform version: v1.36.x |
This 42Crunch API Security Platform release brings new look to the API summary page and adds more features to it. We have also added a new test to API Conformance Scan v2 and continued to improve the Scan v2 in v1-compatible mode.
New features
The following are the new features and improvements to the existing ones in this release.
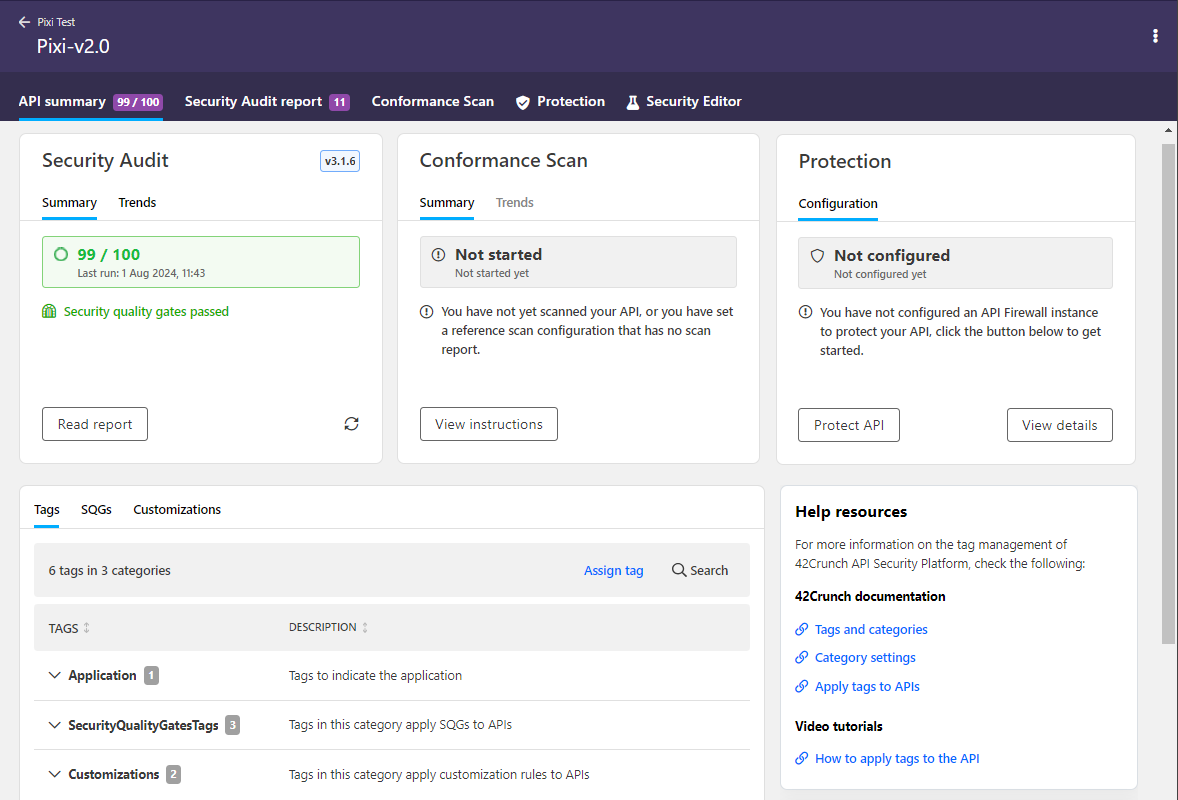
Improved API summary page
We have tweaked how details are shown on the API summary page. You can still see the important details of your API at a glance, but we have now grouped tags, security quality gates (SQGs), and customization rules to their dedicated tabs and also added some new features:
- Quickly see which tags from which categories the API has and what customization rules or SQGs they apply.
- Check how the criteria from different SQGs combine and which has the strictest criteria for each section, to better understand why the API might keep failing SQGs.
- View a list of all the customization rules applied to the API.
- Find relevant documentation and video tutorials through the links to help resources.
Improvements to Conformance Scan
For both Scan v1 and Scan v2, we have fixed how scan configuration is generated when the items property of an array specifies null.
Scan v2
We have added a new test to Scan v2: response-body-badformat-scan. This test uncovers API responses where the response body does not conform to the OpenAPI definition of the scanned API. In addition, we have fixed a bug in reporting excessive data exposure.
We have also removed some of the read-only restrictions on the Scan v2 in v1-compatible mode: you can now change the endpoint, authentication settings, and runtime settings of the existing scan configuration every time you run the scan. However, you cannot go to edit the configuration itself. The same runtime settings are configurable on the UI as when running Scan v1 on the platform.
We continue to make improvements to Scan v2 in v1-compatible mode in upcoming releases and welcome any feedback.
Scan v1
We have clarified how the reference scan configuration for Scan v1 is shown on the UI. Because unlike with Scan v2, in Scan v1 the underlying scan configuration for an API is directly based on the OpenAPI definition and remains the same regardless of where it is run (in 42Crunch Platform or on premises), if you set a Scan v1 configuration as the reference scan configuration, the reference label is shown on both scan v1 configurations. The results shown on the API summary page are from the latest scan regardless where it was run.
Compatibility
This section lists the compatible Docker images for some of the components of 42Crunch API Security Platform, as well as other possible compatibility details.
API Firewall images
This release is compatible with the following API Firewall images:
42crunch/apifirewall:v1.1.3- Support for
x-42c-forward-optionsandx-42c-caseless-paths - Fixed serialization when validating path parameters in the OpenAPI definition that have
oneOforanyOf - Upgrade to
httpd-2.4.61(CVE-2024-39884, CVE-2024-36387, CVE-2024-38472, CVE-2024-38473, CVE-2024-38474, CVE-2024-38475, CVE-2024-38476, CVE-2024-38477, CVE-2024-39573)
- Support for
42crunch/apifirewall:v1.1.2- Fixed schema validation of a nullable value when the value is
null
- Fixed schema validation of a nullable value when the value is
42crunch/apifirewall:v1.1.1- Upgrade to
httpd-2.4.59(CVE-2023-38709, CVE-2024-24795, CVE-2024-27316, CVE-2023-45802, CVE-2023-43622) - Upgrade to
openssl-3.1.6(CVE-2024-2511, CVE-2023-5678, CVE-2024-0727) - Support for the custom blocking mode
- Fixed handling of query parameters when the property
requiredis not explicitly defined
- Upgrade to
42crunch/apifirewall:v1.0.25- Upgrade to
go-1.21.1(CVE-2023-39319, CVE-2023-39318, CVE-2023-3978, CVE-2023-29409) - Upgrade to
openssl-1.1.1w(CVE-2023-4807, CVE-2023-3817, CVE-2023-3446)
- Upgrade to
42crunch/apifirewall:v1.0.24- Upgrade to
httpd-2.4.57(CVE-2023-25690, CVE-2023-27522) - Upgrade to
openssl-1.1.1u(CVE-2023-2650, CVE-2023-0465, CVE-2023-0466, CVE-2023-0464) - Support for multiple API key security schemes with the same name
- Fixed the handling of content
media-typedeclared as opaque string in response validation - Fixed request body handling when API Firewall is set to non-blocking mode.
- Obfuscated headers (except
Host) in transaction logs when the targeted API is unknown - New versions of JWT validation protections (
x-42c-jwt-validation-ec_0.2,x-42c-jwt-validation-rsa_0.2,x-42c-jwt-validation-hmac_0.2)- Validating the
scopeclaim of OAuth2 JWT tokens - Connecting to the JWKS server through a remote forward proxy
- Validating the
- Upgrade to
42crunch/apifirewall:v1.0.23- Health check over SSL
- The environment variable
PLATFORM_HOST - Fixed the handling of
multipart/form-datarequests - Upgrade to
openssl-1.1.1t - Upgrade to
httpd-2.5.55 -
Upgrade to
apr-util-1.6.3
42crunch/apifirewall:v1.0.22- Fixed JWT signature validation
- Allowed plain string content definition
- Upgrade to
openssl-1.1.1s - Upgrade to
libexpat 2.5.0 - Upgrade to
libapreq 2.17 - Upgrade to
libjansson 2.14 - Upgrade to
libjose 11 - Upgrade to
libmaxminddb 1.7.1
42crunch/apifirewall:v1.0.21- Fixed
contenthandling in non-body parameters - HTTP status response code synchronization with Conformance Scan default expectations
- Fixed
42crunch/apifirewall:v1.0.20- Upgrade to
openssl-1.1.1o(CVE-2022-2274, CVE-2022-2097) - Fixed decreasing the number of active instances when firewall shuts down abruptly
- Upgrade to
42crunch/apifirewall:v1.0.19- Upgrade to
httpd-2.4.54(CVE-2022-26377, CVE-2022-28330, CVE-2022-28614, CVE-2022-28615, CVE-2022-29404, CVE-2022-30522, CVE-2022-30556, CVE-2022-31813)
- Upgrade to
42crunch/apifirewall:v1.0.18- Upgrade to
openssl-1.1.1o(CVE-2022-0778, CVE-2022-1292, CVE-2022-1343, CVE-2022-1434, CVE-2022-1473) - Proper handling of the properties
readOnlyandwriteOnlyfrom the OpenAPI Specification (OAS) in schemas
- Upgrade to
All previous image versions have been deprecated and are no longer supported.
When you switch the version of the API Firewall image, you must reconfigure any existing protection configurations so that they work with the new version. For more details, see Reconfigure API Protection.
Conformance Scan images
This release is compatible with the following Conformance Scan images for running it on-premises.
Scan v2
42crunch/scand-agent:v2.0.10- New test
response-body-badformat-scan - Fixed scan configuration creation when
itemsisnull - Fixed excessive data exposure reporting
- New test
We highly recommend that you switch to the latest version to take the full advantage of the new features and security improvements.
42crunch/scand-agent:v2.0.9- Scan v2 in v1-compatible mode
- Support for
Acceptheaders - Upgrade to
Golang 1.22.5(CVE-2024-24789, CVE-2024-24790, CVE-2024-24791)
42crunch/scand-agent:v2.0.8- New test
path-item-method-not-allowed-no-authn-scan - Support for
apiConnectivityCheck,maxTimeoutRetryAttempts, andrequestHeaderNameRequestType - Fixed implementation of
reportIncludeRequestBodyandreportIncludeResponseBody - Fixed handling of lookahead and lookbehind assertion references in regular expressions
- New test
42crunch/scand-agent:v2.0.7- Upgrade to
Golang 1.22.3(CVE-2020-8559, CVE-2024-24788)
- Upgrade to
42crunch/scand-agent:v2.0.6- Lax testing mode
- Fixed generating conformance test requests when multiple required properties are defined
42crunch/scand-agent:v2.0.4- Numeric values exceeding the limits of
float64presented as strings
- Numeric values exceeding the limits of
42crunch/scand-agent:v2.0.3- Upgrade to
Golang 1.21.5(CVE-2023-45284, CVE-2023-45283, CVE-2023-39326, CVE-2023-45283) - New scan report
- Tests
parameter-header-contenttype-wrong-scanandpartial-security-accepted - Support for
reportIncludeRequestBody,reportIncludeResponseBody,reportMaxRequestSizeHappyPath,reportMaxRequestSizeTest - Improved logging for runtime limit
- Heartbeat check
- Upgrade to
All previous image versions have been deprecated and are no longer supported.
Scan v1
42crunch/scand-agent:v1.22.18- Fixed scan configuration creation when
itemsisnull
- Fixed scan configuration creation when
We highly recommend that you switch to the latest version to take the full advantage of the new features and security improvements.
42crunch/scand-agent:v1.22.17- Upgrade to
Golang 1.22.5(CVE-2024-24789, CVE-2024-24790, CVE-2024-24791)
- Upgrade to
42crunch/scand-agent:v1.22.16- Upgrade to
Golang 1.22.3(CVE-2020-8559, CVE-2024-24788)
- Upgrade to
42crunch/scand-agent:v1.22.15- Fixed handling of query parameters in request generation
- Fixed generating conformance test requests when multiple required properties are defined
42crunch/scand-agent:v1.22.14- Upgrade to
Golang 1.21.5(CVE-2023-39326, CVE-2023-45283)
- Upgrade to
42crunch/scand-agent:v1.22.13- Upgrade to
Golang 1.21.3(CVE-2023-45284, CVE-2023-45283) - Heartbeat check to keep the connection to 42Crunch Platform active in case of extremely long scans
- Fixed handling of
exampleandx-42c-sample
- Upgrade to
42crunch/scand-agent:v1.22.12- Support for
text/plainas content type - Support for
read-onlyproperties
- Support for
-
42crunch/scand-agent:v1.22.11- Upgrade to
Golang 1.20.7(CVE-2023-39319, CVE-2023-39318, CVE-2023-3978, CVE-2023-29409) - Fixed handling of
<and>characters in the request payload - Improved handling of content not supported by Conformance Scan
- Upgrade to
42crunch/scand-agent:v1.22.9- Performance improvements to scan configuration generation
- Better memory handling when generating array items of the type
filefor scan requests - Better handling of expired customization rules
- Improved JSON schema validation for UTF-8 strings
42crunch/scand-agent:v1.22.8- Upgrade to
Golang 1.20.4(CVE-2022-41716, CVE-2022-41717, CVE-2022-41720, CVE-2022-41722, CVE-2022-41723, CVE-2022-41724, CVE-2022-41725, CVE-2023-24532, CVE-2023-24534, CVE-2023-24536, CVE-2023-24537, CVE-2023-24538, CVE-2023-24539, CVE-2023-24540, CVE-2023-29400)
- Upgrade to
42crunch/scand-agent:v1.22.7- Updates to regular expression library
42crunch/scand-agent:v1.22.6- Fixed regular expressions handling
In some rare cases, certain regular expression patterns could send the on-premises scan to an infinite loop, and the process would not finish. This image version fixes that, so if you are experiencing on-premises scan hanging, we recommend upgrading from the previous scan images to this one.
- Fixed regular expressions handling
42crunch/scand-agent:v1.22.4- Improved array iteration
All previous image versions have been deprecated and are no longer supported.
Changed behavior
Depending on your API, the new test response-body-badformat-scan in Conformance Scan v2 can increase the number of found issues.
Deprecated components
The free community organization in 42Crunch Platform has been deprecated on July 31, 2024 and is no longer available. For further information, see Community Organization End of Service Notice.
Known issues
This release has the following known issues.
Manage teams permission not shown on list of users
The permission to manage teams is not yet shown on the list of users in your organization, but you can view all permissions that a user has by clicking the permission column. This permission also does not yet have a shortcut that you could use when searching by permission.
These will be fixed in a future release.
Changing tagging on an API may trigger an unrelated error on the UI
Sometimes applying tags to or removing them from an API may trigger an unrelated error on failing to fetch the SQG approval report for the API. This happens if the API in question has been scanned on-premises and the scan has finished after you arrived on the API Summary page, because the UI cannot find the latest on-premises scan report and the associated approval report. Refreshing the page gets the latest reports and resolves the issue.
Tagging and untagging the API is not affected by this error: tags get correctly applied and removed in any case.
This will be fixed in a future release.
Data dictionary duplication
Duplicating a data dictionary does not yet duplicate the values in it.
This will be fixed in a future release.
Scan customization rules may lead to no response codes being accepted.
In some cases, scan rules can lead to HTTP status response codes in API responses that are normally expected (for example, HTTP 401 or HTTP 404) to be treated as unexpected. This in turn can lead to a false positive in the scan results.
By default, the expected HTTP status response codes that are defined in scan rules applied to the scanned API take preference over the response codes that Conformance Scan would otherwise expect. However, this can cause problems in scan process if your scan rule only skips header or response body analysis but does not define any expected response codes, either for happy path requests or for particular test IDs. This results in the scan rule to have null defined as the expected response code, and because the scan rule takes preference over the default scan behavior, no response codes except null are accepted. This in turn means that some tests are incorrectly flagged as returning unexpected response codes when they were in fact successful.
We are currently investigating the best way how to reconcile the designed behavior of Conformance Scan and scan rules in these cases, and this issue will be fixed in a future release.